Inside Kraken Security Labs: Crypto Domain Hijacking
Learn how to better identify and protect yourself from crypto domain hijacking with Kraken Security Labs.

If you leave digital footprints, (spoiler: you do) then you can be followed. Just because you shut down an account, switched domain names or got a new Twitter handle does not mean that your old tracks disappear. In fact, the footprints you leave online can become critical vulnerabilities.
At Kraken Security Labs, we work to discover possible attack vectors against the crypto community before the bad guys do. One of the best ways to do that is to figure out how we might attack ourselves and specifically our CEO, Jesse.
Disclaimer: If you work at a company that does not have the same rigorous security stance as Kraken, please think twice before trying to hack your CEO.
- Scoping the Target
Any good attack starts with recon, and we stumbled upon an interesting tweet from years ago:

Some quick searching revealed that many people made similar tweets in 2014, including Tyler and Cameron Winklevoss, who backed the project.


We visited onename.io and were greeted with a blank Heroku page (Heroku is a cloud platform used for building websites), indicating that the site was no longer set up but it was not decommissioned either.

- At this point, the vulnerability was clear. Anyone with a Heroku account could add this domain to their profile and serve whatever content they wanted.
- This domain takeover attack is so common in the bug bounty community that one hacker has even maintained a database (https://github.com/EdOverflow/can-i-take-over-xyz) to check on common dangling services.
- Claiming the domain was as simple as upgrading to a premium Heroku account and adding the domain to a project, no additional checks were required from Heroku’s side since the DNS records already existed.
- We later learned that onename.io was replaced by onename.com around 2015. In fact, Jesse’s profile had been replicated to onename.com, which showed that onename was a service where users could verify their PGP key and bitcoin receiving address.

- Setting the Trap
We immediately added the domain to our Heroku account and began collecting logs to see if any users would visit the site.

- We then cloned Jesse’s page and set it to capture any usernames and passwords that were submitted.
- We edited the Bitcoin receiving address and PGP keys to ones that we controlled and added Javascript code that would scrape information about his browser, platform, and location.
- We could also potentially inject malware, such as the two recent Firefox 0-days used against Coinbase.
- Action Stations
With the attack ready, we needed Jesse to visit a link that he had previously tweeted. We knew that timing was important and so we leveraged Twitter notifications and a service called Zapier to let us know when Jesse was active on the platform (i.e., when he was tweeting or liking tweets).
- We created fake accounts and began replying to the 2014 tweet, hoping that a curious Jesse would check out our malicious site at onename.io.

- This didn’t work. No additional users clicked the link even though we actually did send a donation to the fake address. We decided to switch tactics and move from generic praise to minor annoyance.
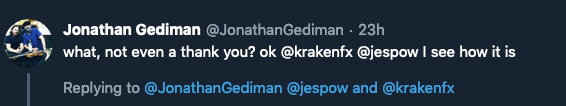
- Even though this reply was sent within seconds of Jesse browsing Twitter, we still didn’t get any visits. Perhaps it was the volume, so we created some fictitious back and forth flaming.
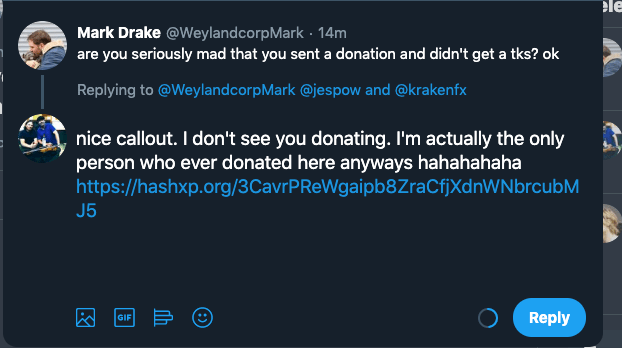
- Finally, a direct quote-tweet referencing the page in question was attempted. While this didn’t seem to initially work, logs indicated that someone clearly followed the Twitter link to visit the page (instead of a search engine bot following links).

- The recorded information from our tracking, such as user agent, IP address, and referer seemed to confirm that someone following the discussion on Jesse’s timeline clicked the link. We were not able to identify the visitor and wWhile this person viewed our malicious site, they didn’t enter any sensitive information – so kudos to them.
- To The Domain Owner, The Spoils
Though Jesse was our primary target and we didn’t attempt to solicit any other users, we observed hundreds of visits from all over the world for the 4 weeks that the site was online.

World map of all visitors
- Despite being a defunct service, the Onename site seemed to still attract human visitors, mostly from following profile links or other domains that were pointed to it.
- While the majority of traffic was from search bots and scrapers, we observed occasional patterns such as delays, typos, and repeated requests that seemed to point to a human.
- We even observed multiple users attempting to submit their username and password to us.
- These visitors were safely redirected to the actual onename.com website, but an unscrupulous attacker might be able to leverage the inherent trust associated with a domain and passively collect credentials without raising alarms, including from password managers that only check the URL before entering passwords.
- Kraken’s mission is to protect and grow the cryptocurrency ecosystem, so we returned onename.io to Blockstack.org (the owner of onename).
- Takeaways
- Unfortunately, there are very few ways to protect yourself from an attack like this. Without a method for verifying that site is still under the correct ownership (such as PGP signing), a site could be constructed that would be a near-identical copy.
- In our case, site content was actually the same. Encrypt certificates were deployed from Heroku and all pages worked without error – making it really hard to spot any differences or red flags.
- Because of this, it’s crucial for any company to ensure that strict procedures are followed for the decommissioning of old sites and subdomains. Although cloud services can provide an amazing amount of swiftness, the counterbalance to DevOps is strong monitoring.
- Additionally, this is also a friendly reminder that everyone from the client to the service provider needs to remain ever-vigilant against spoofing sites.
- If You See Something, Earn Something
- As you can tell, our security team is always on the lookout for vulnerabilities that may pose a threat to our clients.
- If you’re interested in helping us identify potential bugs on our platform, check out our Bug Bounty program.
- We payout a minimum of $100 for each issue and potentially more for serious threats.



